Access control can also be used to connect clients to particular services, depending on the requested service, the origin of the request, and the host address to which the client connects. Grammar and spelling errors should be expected. I usually send all my logs to a file, use scripts to scan them and e-mail or page people as necessary. Event Soweto school-in collaboration with FinChat September 17, Here is a list, with default values shown where appropriate:. The examples in the rest of this section are related to the hosts.
| Uploader: | Meztizshura |
| Date Added: | 25 January 2005 |
| File Size: | 38.66 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 25028 |
| Price: | Free* [*Free Regsitration Required] |
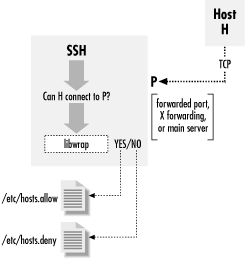
When a client attempts to connect to a network service controlled by xinetdthe super service receives the request and checks for any TCP Wrappers access control rules.
What are the commands? An undotted argument is understood as a level.
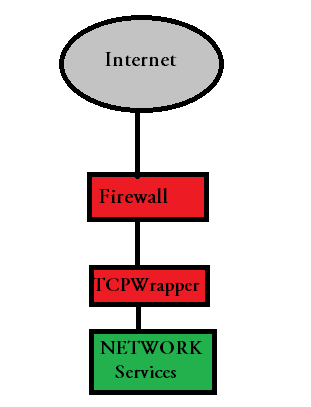
Using TCP Wrappers to control access
The system is invoked after a remote host connects to your computer. Hopefully this summary will get you on the right track.
With TCP wrappers installed the only difference that you call wrapper first with the service as a parameter:. The second rule entry output reports that there are no errors and that the domains are resolvable via the DNS. After the connection has been established, xinetd takes no further part in the communication between the client and the server.
The Tek-Tips staff will check this out and take appropriate action. Now, further assume that we wish to allow access for ssh and telnet using the following IP addresses: Reasons such as off-topic, duplicates, flames, illegal, vulgar, or students posting their homework.
Using TCP Wrappers to control access – IBM Developer
In addition, disruption to DNS service prevents even authorized users from using network services. Sets host access control. You can use PayPal to make a contribution, supporting development of this site and speed up access. Remember, the first match is the important one -- the ALL in hosts. This is for protection against hosts that pretend they have someone else's host address --i.
The Elements of Programming Style: This document is an industrial compilation designed and created exclusively for educational use and is distributed under the Softpanorama Content License.
If access is allowed, xinetd verifies that the connection is allowed under its own access rules for that service.
Solaris 9 SSH already has alx support compiled on. Now, there are a couple of things to note here. X We use cookies to optimize your visit to our website. Financial Humor Bulletin, This allows you to put a message up to the incoming client when a connection is made, or when a connection is denied.
Setup TCP Wrappers on AIX
Access can be controlled per host, per service, or in combinations thereof. In another example from a hosts. I'm running Solaris 8.

For example, let's say that we wanted to enable TCP Wrappers for telnet but not for ftp. The site uses AdSense so you need to be aware of Google privacy policy.
TCP Wrappers Provide Robust Logs
Wrappers allow system administrators to control access of TCP-based services or daemons that are wrappers aware. This is also the case for a rule that spans multiple lines without using the backslash character. For this to be of any use, the remote host must run a daemon that supports the finger protocol. Event Thembisa school collaborate FinChatbot September 19, Examples are given axi.
I have a requirement to check the tcp network connectivity between server it's running on and the list of host's and ports combination. Now, within that directory, create a file for each service daemon.

Комментариев нет:
Отправить комментарий